RST Cloud and SAF Systems Alliance
RST Cloud and SAF Systems Announce Technology Alliance
The other day, Enterprise Security published an article about the RST Cloud and SAF Systems technology alliance.
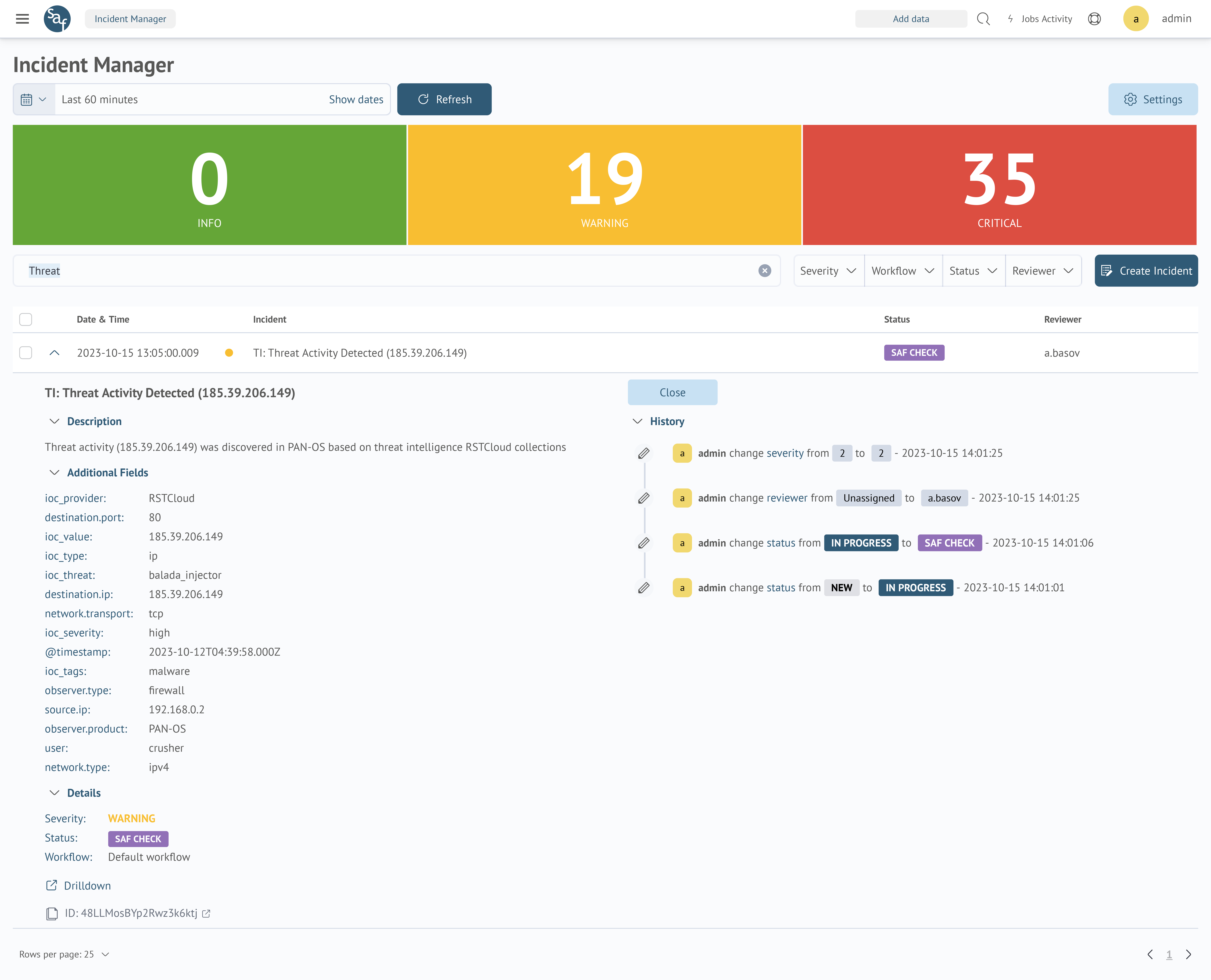
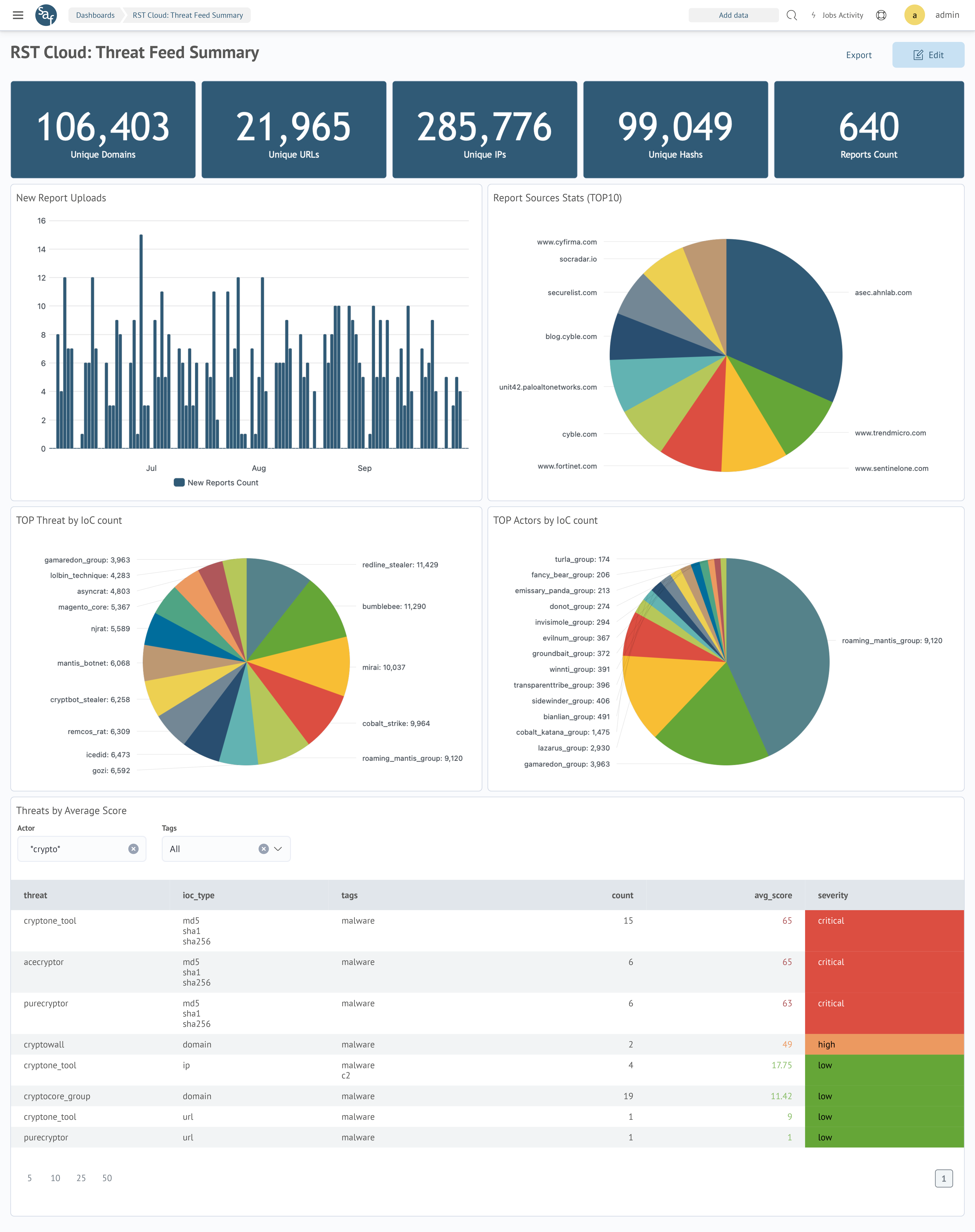
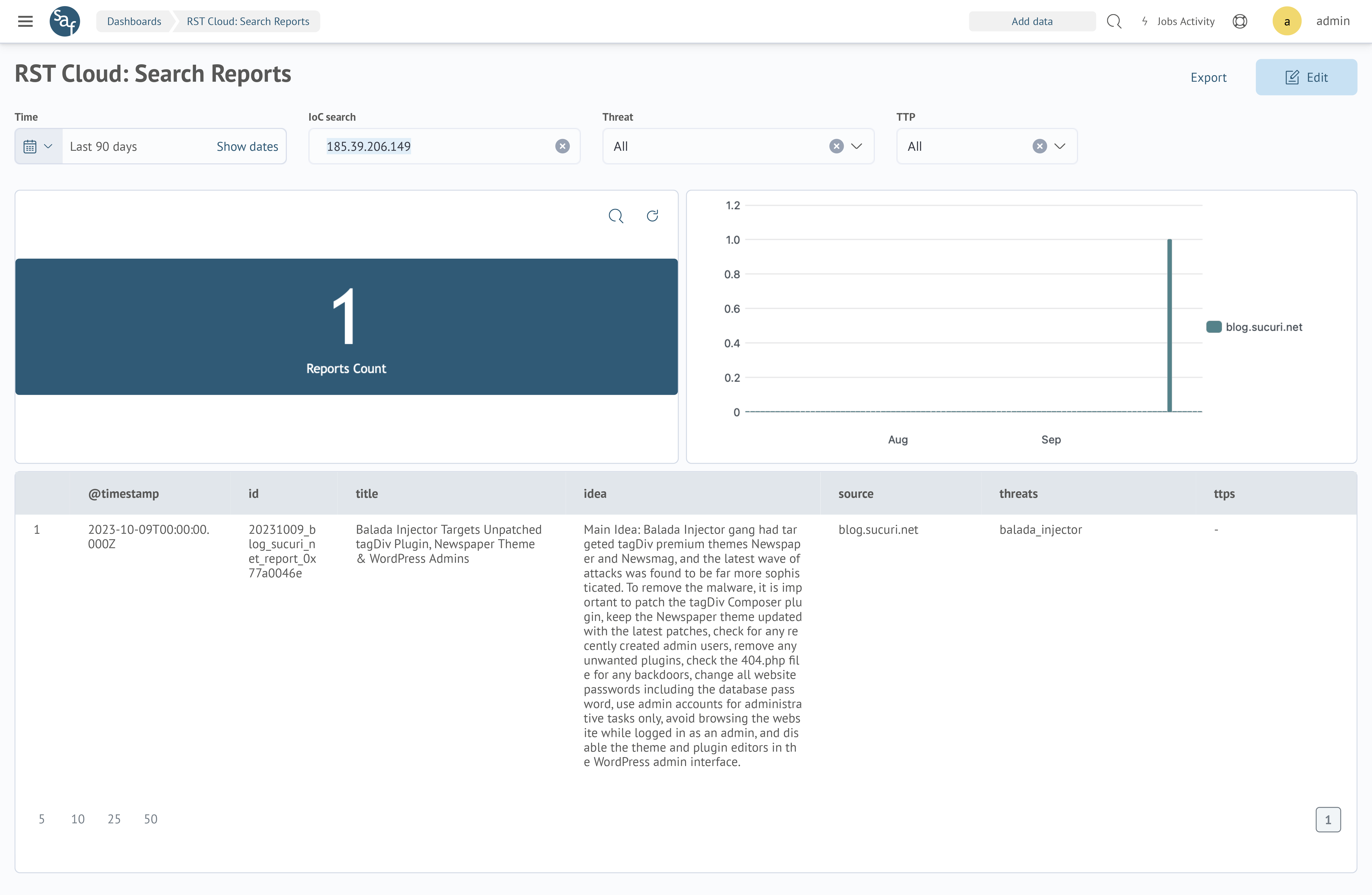
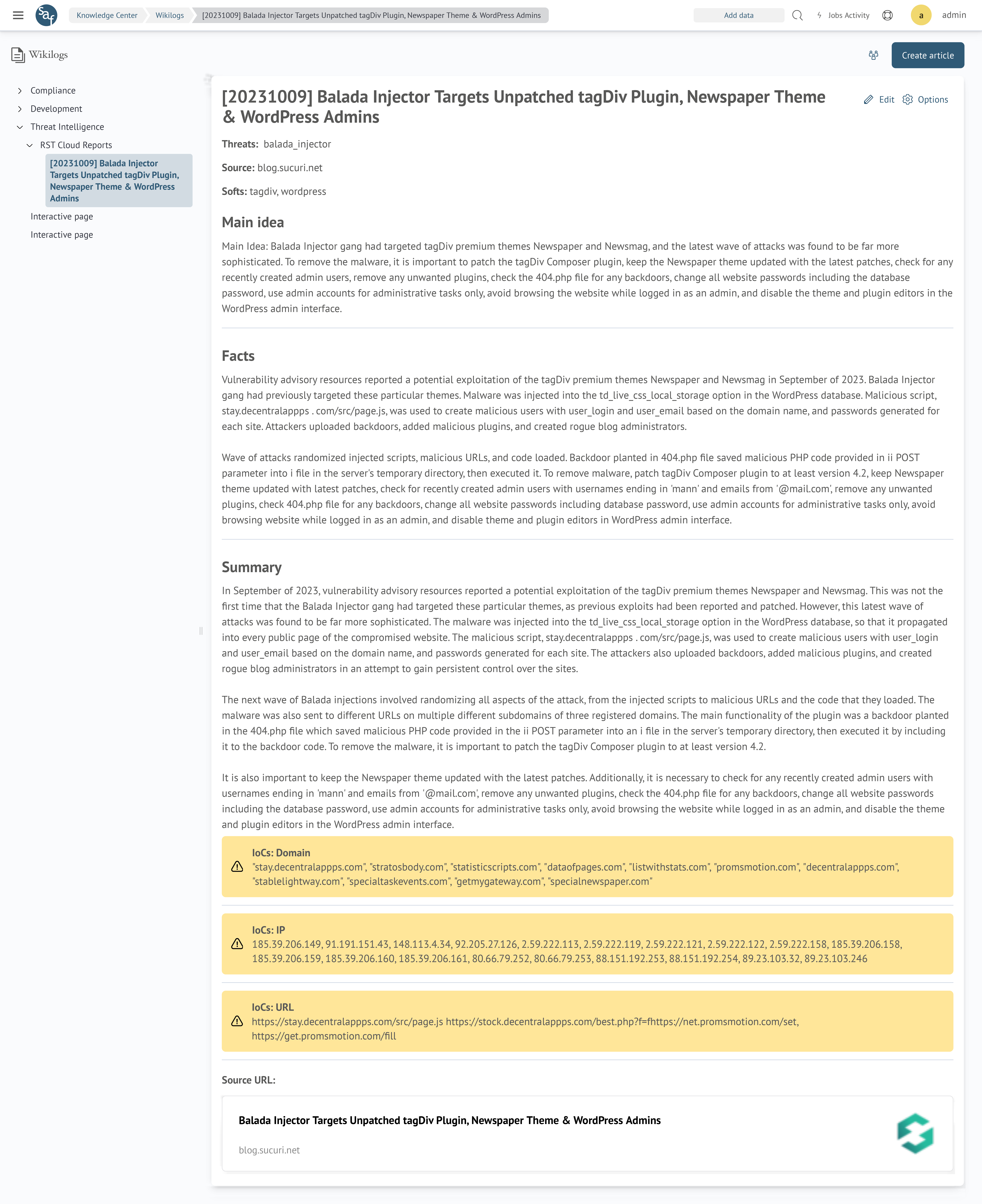
The collaboration will integrate RST Cloud’s Threat Feed and Report Hub products into our Search Anywhere Framework (SAF) solution, enabling enhances incident detection, facilitates efficient incident triage, and reinforces incident response capabilities.
We have joined forces to promote cybersecurity standards in the modern digital world. Our goal is to improve incident detection and to increase the effectiveness of measures to combat the ever-changing challenges of cybersecurity.

Yury Sergeev
CEO of RST Cloud
“The ability to bring CTI data into SAF and access it in real-time empowers the cybersecurity features of the platform.
It significantly optimises the workflow of SOC analysts by saving valuable time and streamlining the decision-making process as now they do not need to switch between different screens and can access the required TI data within the SAF UI. Also, it enhances the quality of response to cybersecurity incidents by providing actionable insights in real-time.”
It significantly optimises the workflow of SOC analysts by saving valuable time and streamlining the decision-making process as now they do not need to switch between different screens and can access the required TI data within the SAF UI. Also, it enhances the quality of response to cybersecurity incidents by providing actionable insights in real-time.”

Alexander Skakunov
SAF Systems founder,
managing partner
managing partner
"This integration allows us to enable our platform with CTI services in an efficient and user-friendly manner, ultimately enhancing the security posture of organisations.
Among the innovative scenarios currently being explored is Threat Hunting, designed to maximise the utilisation of RST Cloud's data within the SAF platform. This partnership aims to harness the full potential of CTI data.”
Among the innovative scenarios currently being explored is Threat Hunting, designed to maximise the utilisation of RST Cloud's data within the SAF platform. This partnership aims to harness the full potential of CTI data.”