Business Intelligence with SAF
More about Business Intelligence
Data has long been one of the most valuable assets of a company, and using BI is a necessity for successful business development.
SAF allows you to effectively track various business metrics and respond promptly to critical changes. All useful information is presented in informative dashboards.
About the case
But let's not talk for long, it's better to show everything.
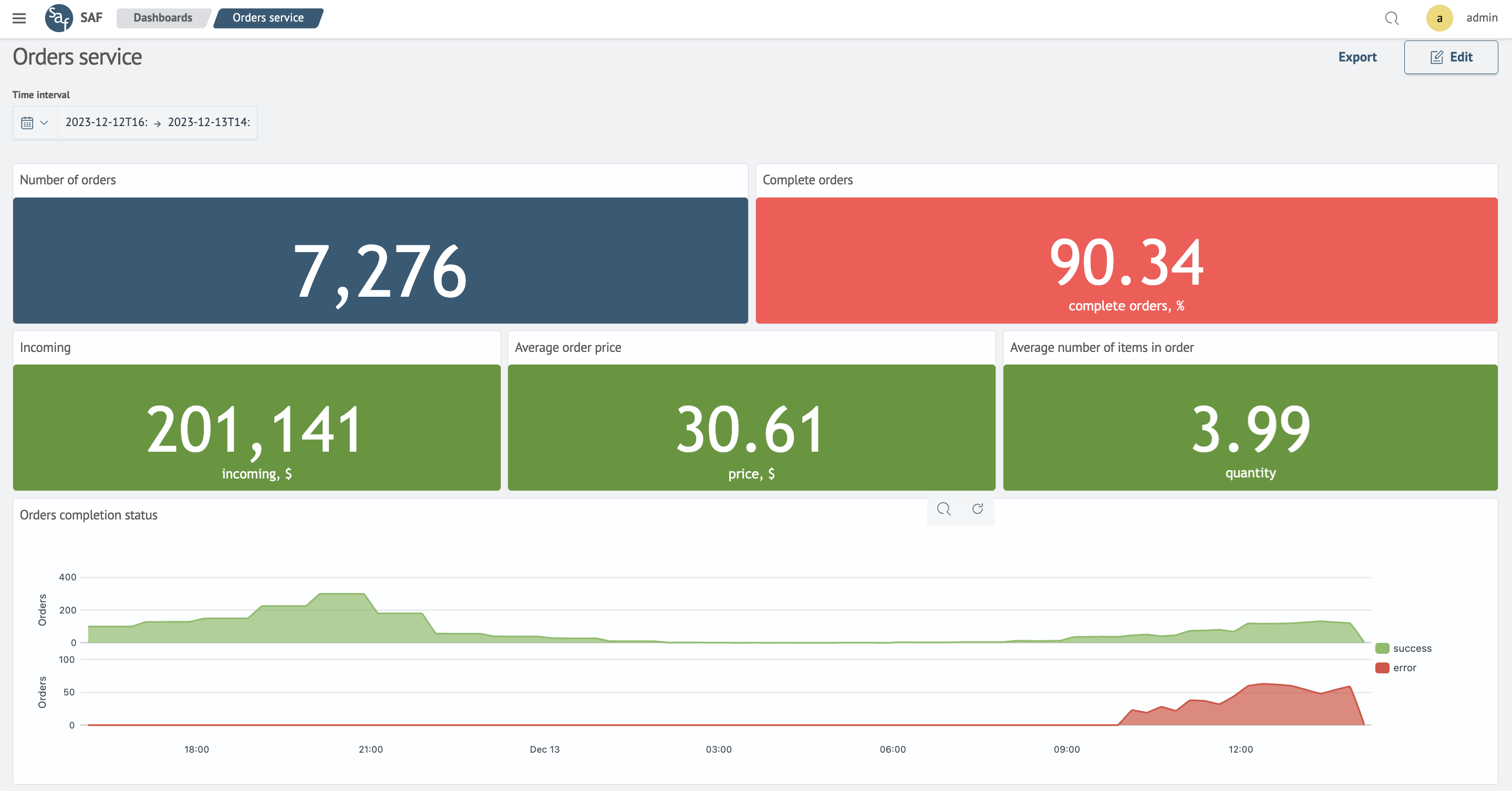
In the video, we check the asset-service model and see that in the business branch, the number of technical support requests has increased. Apparently, customers are facing some issues. Moving to the orders dashboard, we see that the number of successful orders has significantly decreased. For us, this is a bad sign, meaning there are some technical problems.
Quite quickly, we find out that the order service cannot connect to the database. It is overloaded due to suspicious requests from the user GreenRichard.
In previous episodes, we have already discovered that this suspicious user has caused a lot of trouble within our company.
Summarize
-
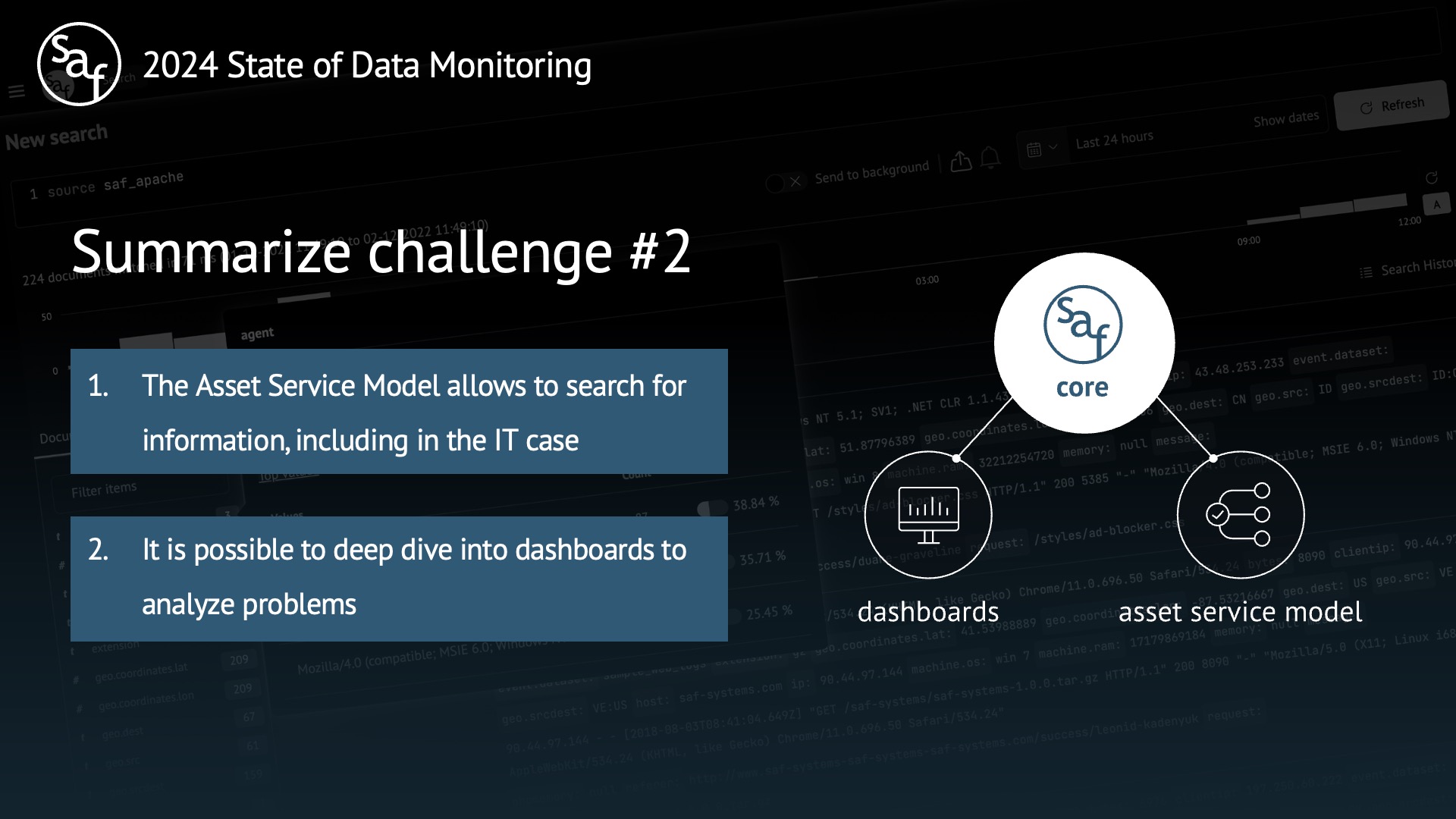
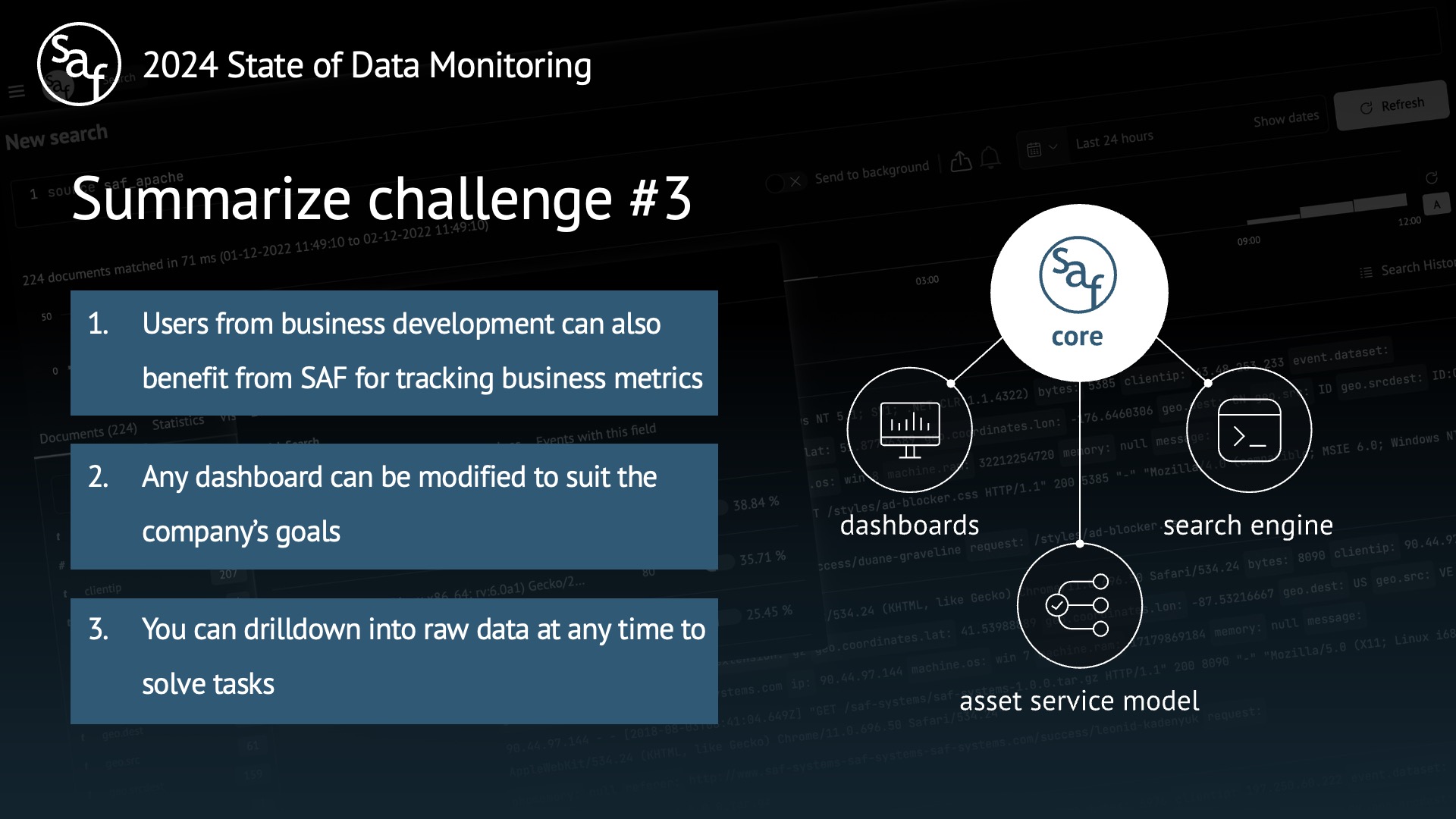
Users from business development can also benefit from SAF for tracking business metrics.
-
Any dashboard can be modified to suit the company’s goals.
-
You can drilldown into raw data at any time to solve tasks.
Thus, we have established that there are some suspicious activities happening in the company, as well as identified who is responsible for it and which other structures have been affected by these events.

Stay informed about all changes in your business and react promptly to critical events with SAF Systems 😉
Pipe TwinTech
innovating integrity: transforming pipeline maintenance with data

-
create a digital twin of the pipeline system
with all data about the pipeline system (the results of the pipeline system diagnostics information about ICCP, ILI, DCGV, CIPS and other surveys, taking into account previous digging and other external factors affecting its operational reliability)
-
conduct a complex pipe conditions analysis
of the pipeline system technical conditions and identify patterns of development of corrosion defects
-
forecasting the development of corrosion in pipes
create Data-Driven models for the development of corrosion defects in the pipeline system using artificial intelligence
-
reduce investment costs for maintenance and diagnostics
The best repair methods are determined for each pipe or section of pipes in the pipeline system. Each pipe in a pipeline system will have its own unique set of data from the time it is included in the system to the time it is replaced. That is, even during local repairs, there are situations when pipes change or replace and during the next in-line inspection, it is not possible to identify the development of corrosion defects on the same pipes.
Pipe TwinTech will allow to identify each such pipes and use the full technical resource of each pipe included in the system.
key features
information included in the dataset

planning local repairs with Pipe TwinTech
Using available inspection and diagnostic results and data regulating the withdrawal of pipeline sections for repair, a medium-term plan for conducting local repairs is formed, with the possibility of analyzing its impact on the pipeline's condition and monitoring the results of its implementation.
During the planning stage, local repairs needed to be carried out are displayed, along with all characteristics of pipes and defects included in the local repair plan.
A responsible person is appointed to conduct the excavation of pipes for inspection and repair. If repair is required based on diagnostic results, the type of repair is approved. Repairs are carried out, and the results are recorded in the system.
summary statistics in one place
Monitoring the results of the ILI comparison (the number of matched and non-matched pipes, the number of pipes with corrosion defects and other anomalies), tracking statistics on groups of various defects divided into sections between crane platforms, analysis of summary statistics for each pipe, taking into account the comparison of all ILI.
detailed information about the condition of pipes
Track the details of the pipe survey taking into account the ILI comparison. It is possible to detect a deterioration in the condition of the pipe or an incorrect interpretation of the results of one of the ILI.
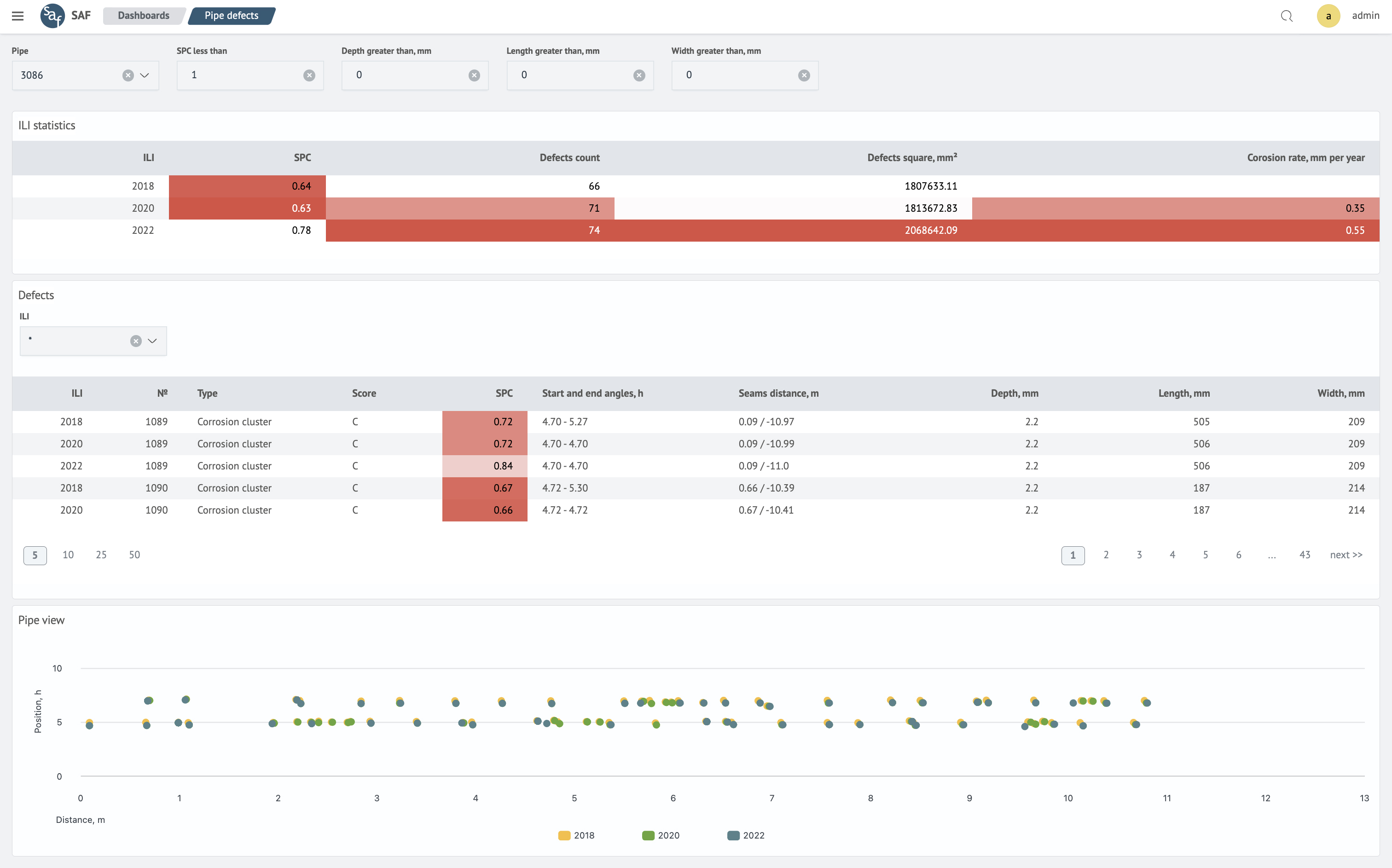
optimization of parameters for local pipeline repair plan
The capability to optimize parameters for the local pipeline repair plan has been implemented, allowing for the automatic creation of extended excavations in case of defects on pipes located in close proximity to each other.
comparison of ILI data from different years and sections
Track the development of defects by type and quantity per kilometer of pipeline by comparing data from in-line inspections from previous periods.
detailing of the repair area
You can monitor the repair area and get the necessary statistics, taking into account the comparison of the available ILI.
key business indicators (expected outcomes)

Pipe TwinTech
innovating integrity: transforming pipeline maintenance with data

-
create a digital twin of the pipeline system
with all data about the pipeline system (the results of the pipeline system diagnostics information about ICCP, ILI, DCGV, CIPS and other surveys, taking into account previous digging and other external factors affecting its operational reliability)
-
conduct a complex pipe conditions analysis
of the pipeline system technical conditions and identify patterns of development of corrosion defects
-
forecasting the development of corrosion in pipes
create Data-Driven models for the development of corrosion defects in the pipeline system using artificial intelligence
-
reduce investment costs for maintenance and diagnostics
The best repair methods are determined for each pipe or section of pipes in the pipeline system. Each pipe in a pipeline system will have its own unique set of data from the time it is included in the system to the time it is replaced. That is, even during local repairs, there are situations when pipes change or replace and during the next in-line inspection, it is not possible to identify the development of corrosion defects on the same pipes.
Pipe TwinTech will allow to identify each such pipes and use the full technical resource of each pipe included in the system.
key features
information included in the dataset

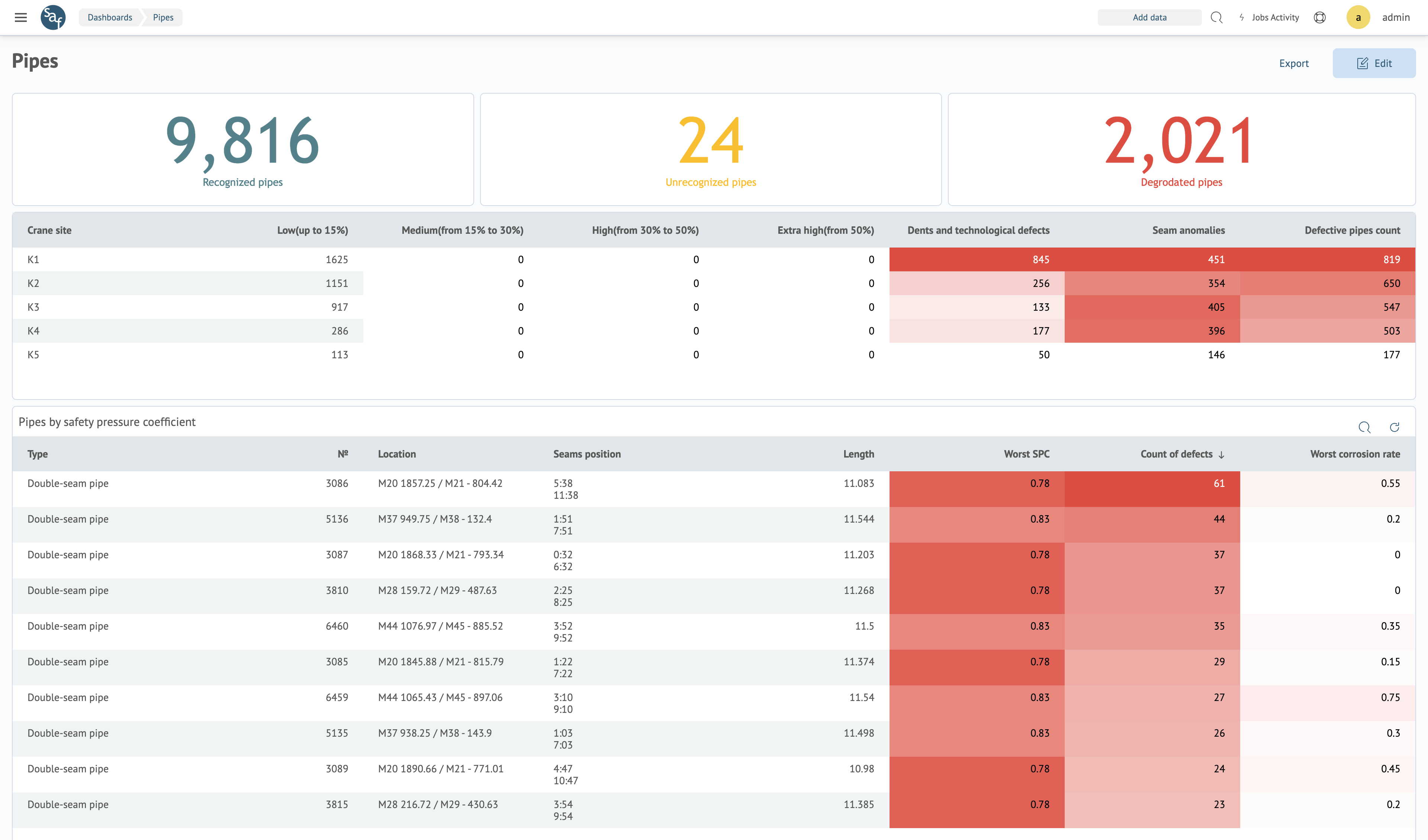
summary statistics in one place
Monitoring the results of the ILI comparison (the number of matched and non-matched pipes, the number of pipes with corrosion defects and other anomalies), tracking statistics on groups of various defects divided into sections between crane platforms, analysis of summary statistics for each pipe, taking into account the comparison of all ILI.
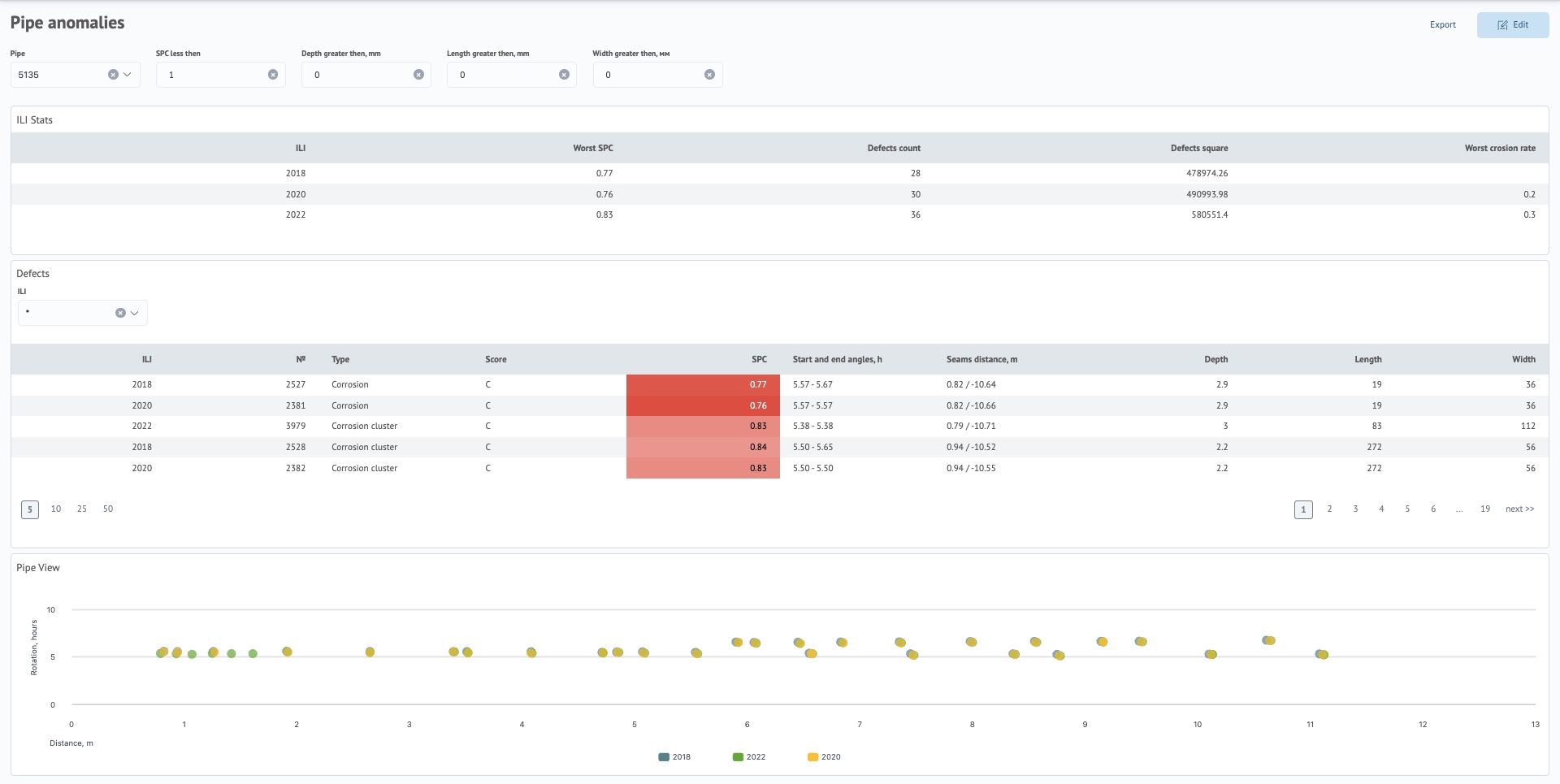
detailed information about the condition of pipes
Track the details of the pipe survey taking into account the ILI comparison. It is possible to detect a deterioration in the condition of the pipe or an incorrect interpretation of the results of one of the ILI.
development of repair plans taking into account the ILI comparison
You can set various parameters for preparation a repair plan and compare the received plans to select the most optimal and less costly in terms of resources.
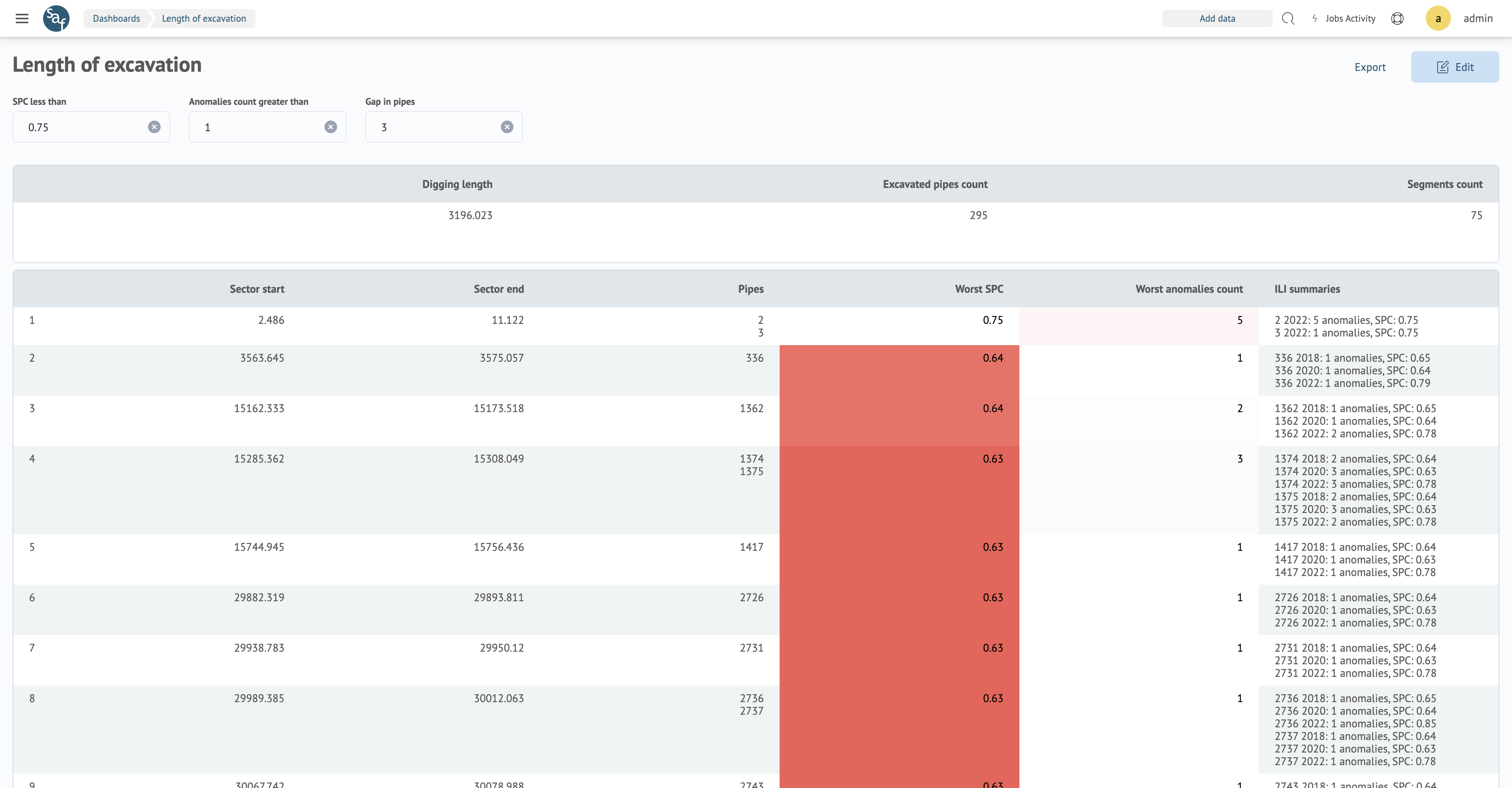
detailing of the repair area
You can monitor the repair area and get the necessary statistics, taking into account the comparison of the available ILI.
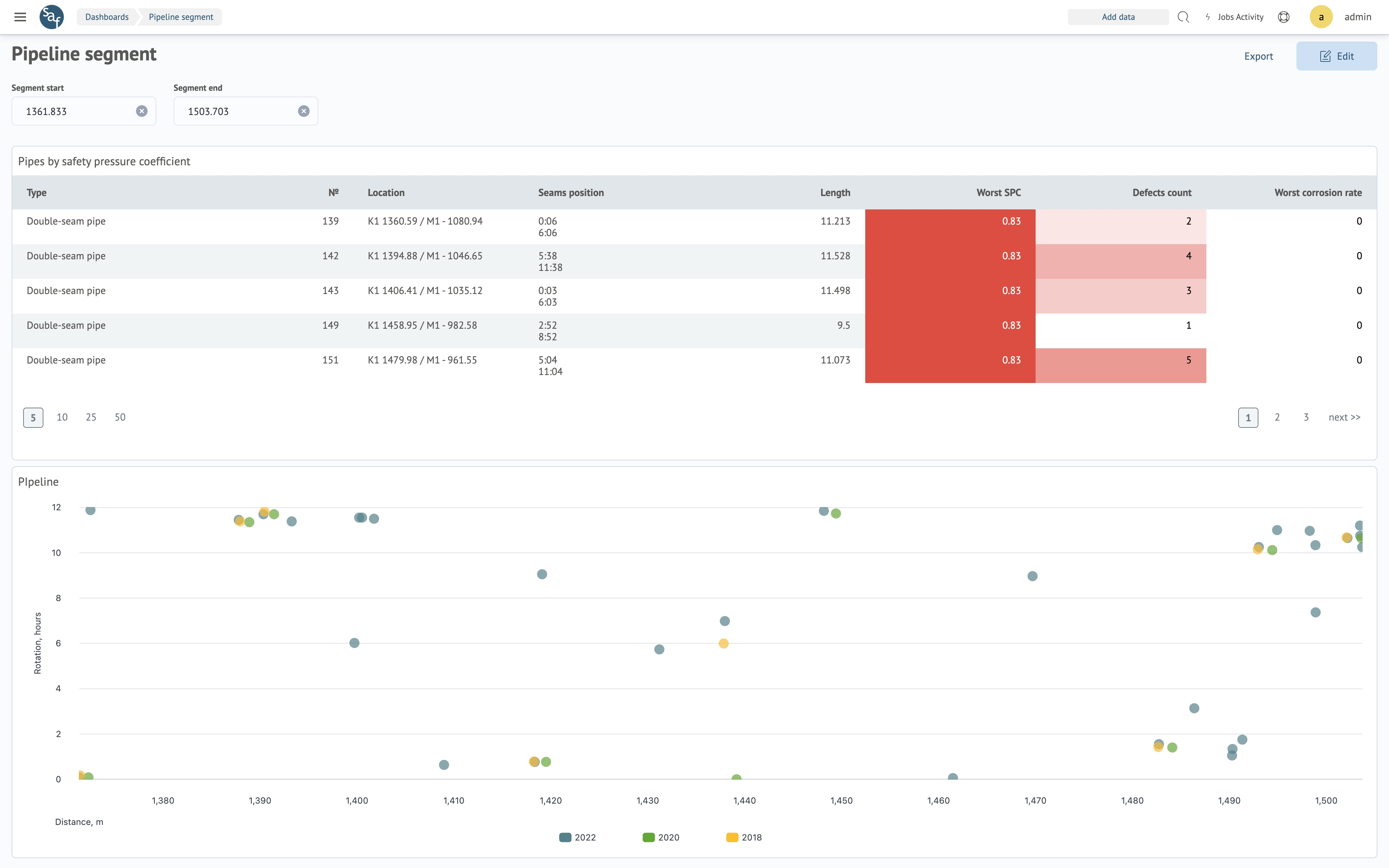
key business indicators (expected outcomes)

Recording of the webinar
2024 State of Data Monitoring
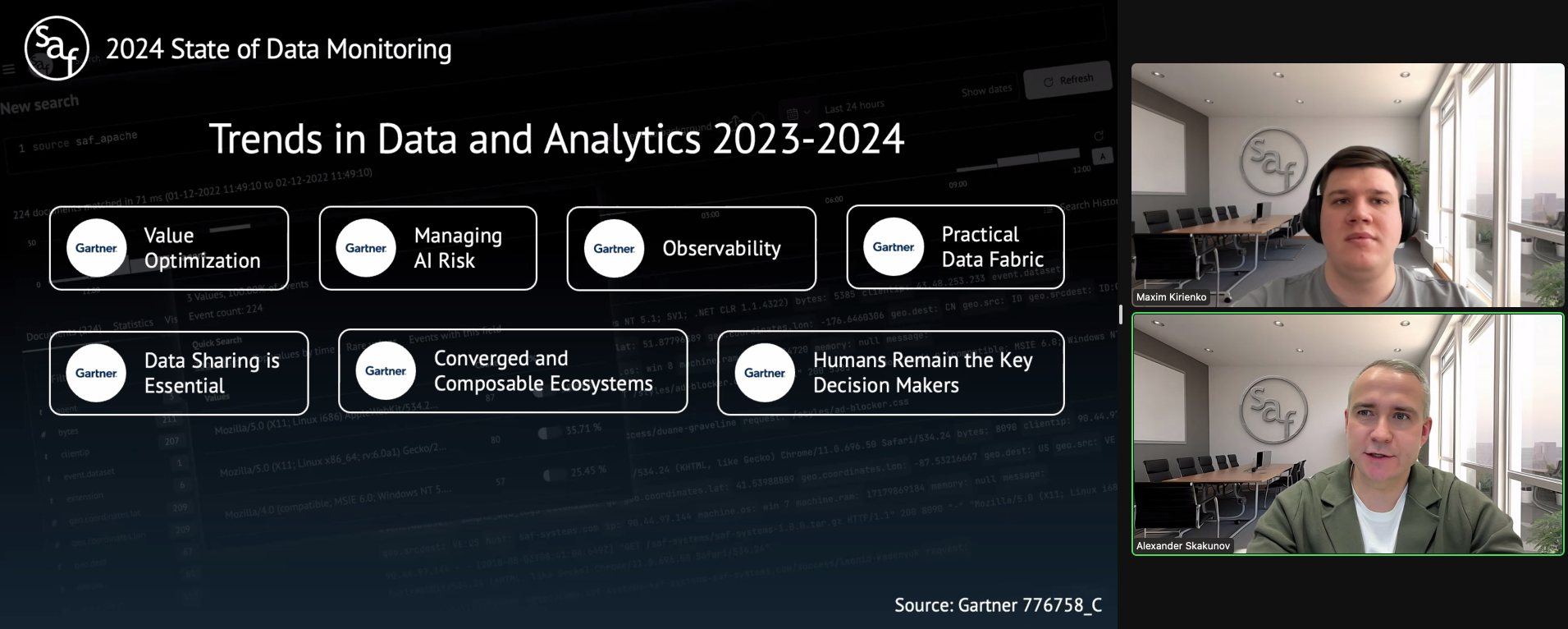
In the webinar we discussed the latest trends in data monitoring and shared our predictions for 2024. We also demonstrated the implementation of these trends in the SAF product using a case study. We would like to thank everyone for their participation and interesting questions.
And for those who could not join us yesterday, we have prepared a recording. You can watch it at:
Watch the recording in Zoom
Timecodes for your convenience
-
01:25
About SAF System
-
02:41
Trends in Data and Analytics 2023-2024
-
06:00
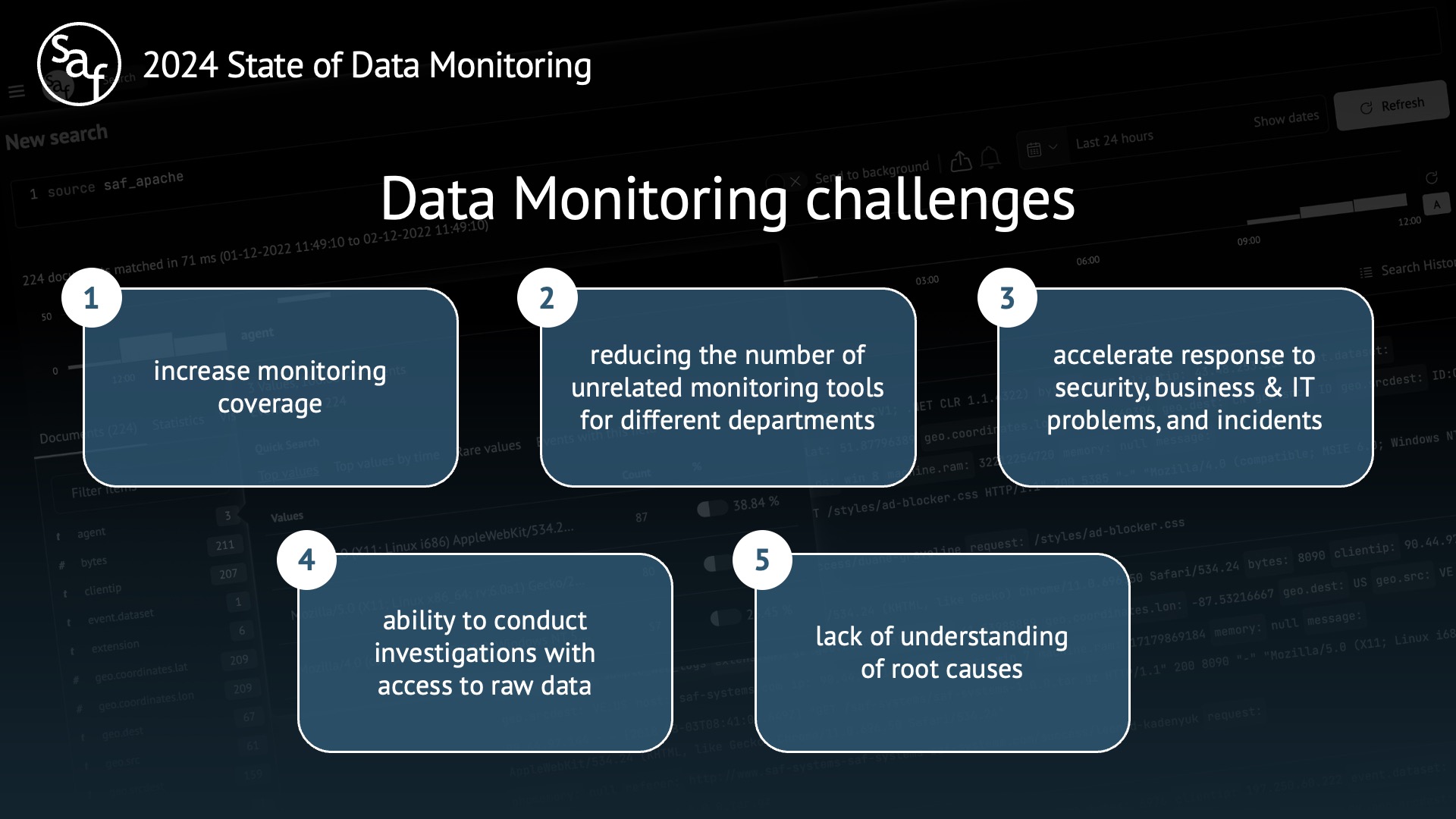
Data Monitoring challenges
-
08:10
About the case
-
10:00
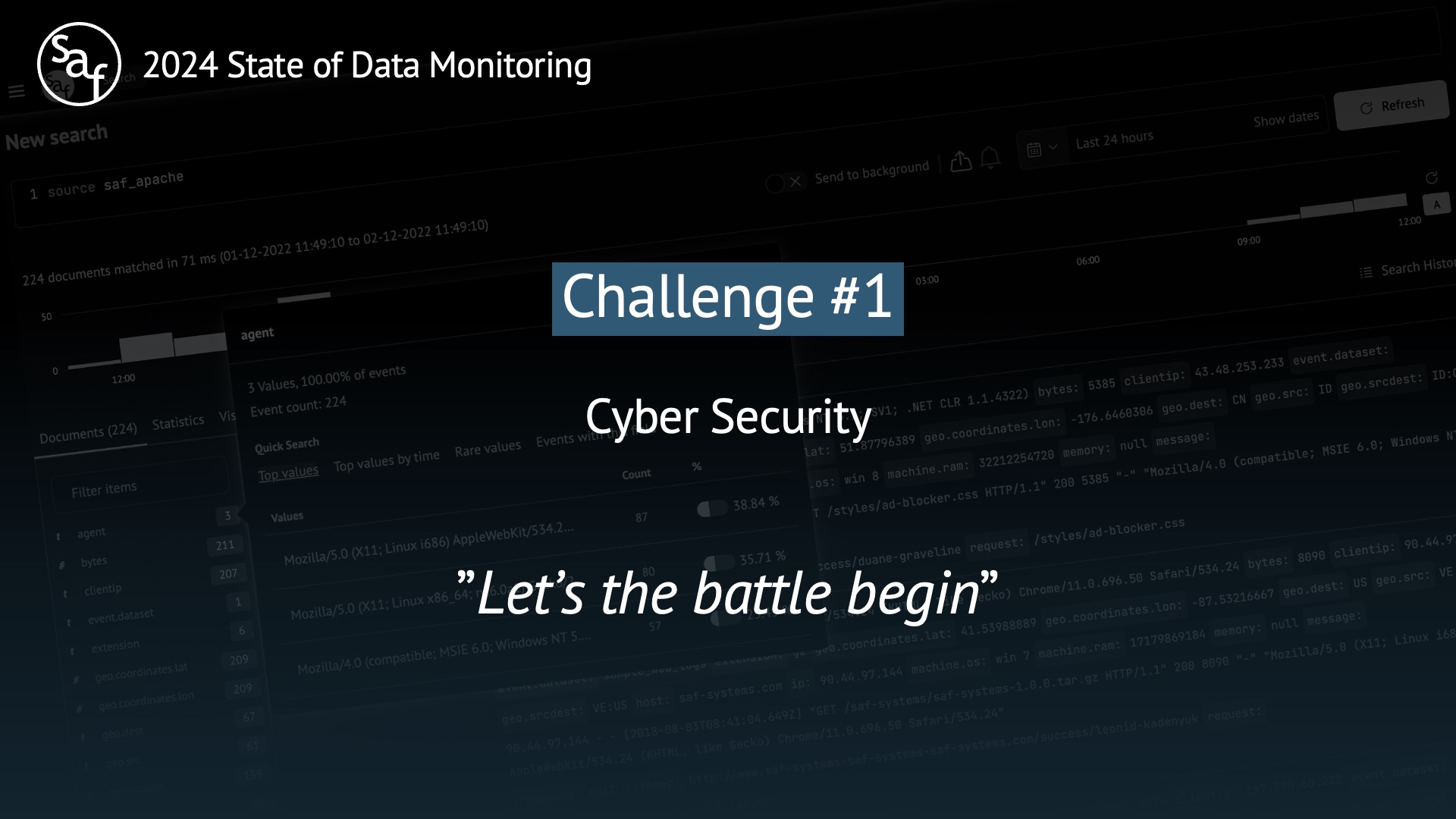
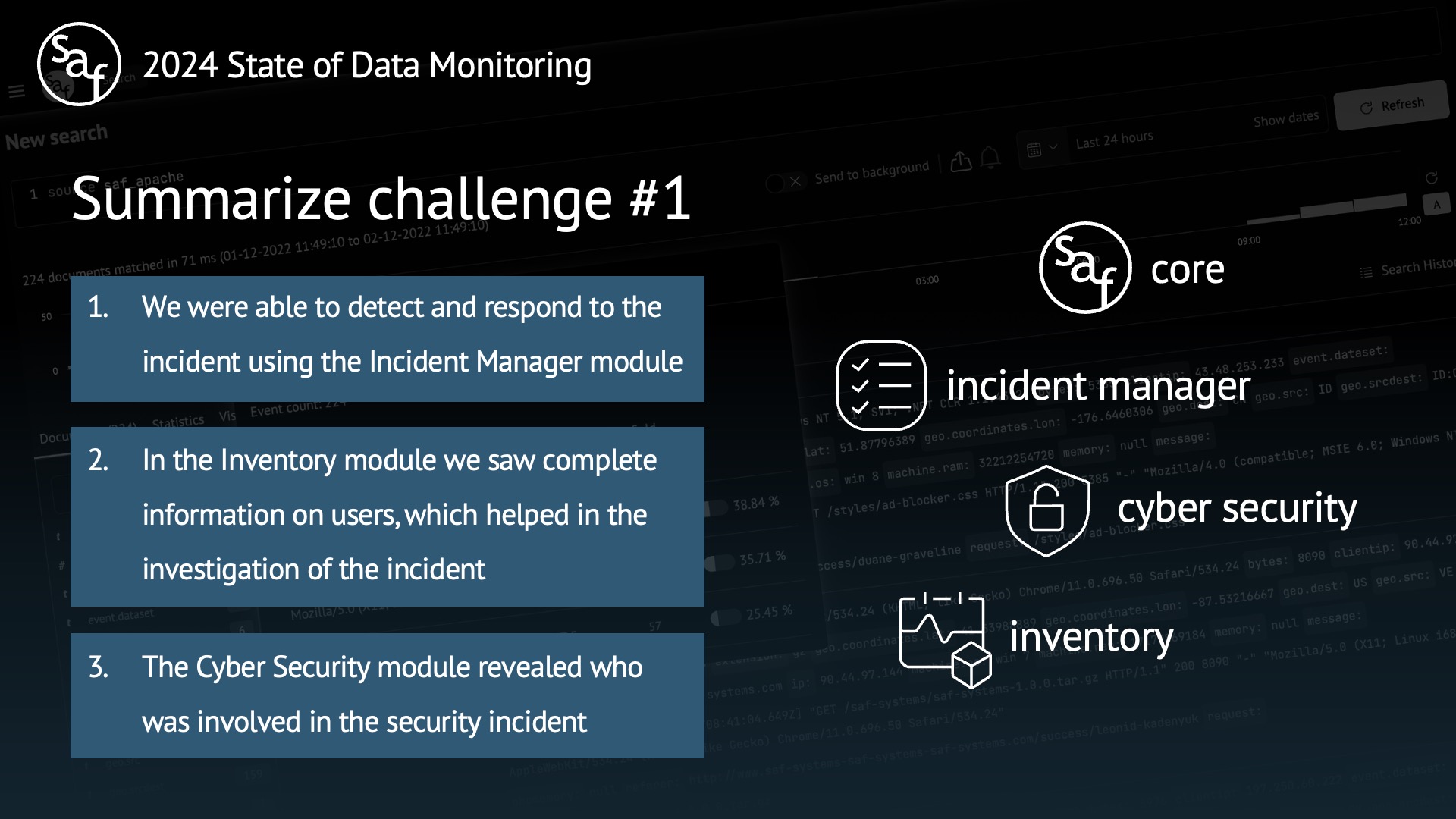
Challenge #1 Cyber Security (Core, Incident Manager, Inventory)
-
17:33
Challenge #2 IT Operations (Core: Dashboards, Asset Service Model)
-
22:25
Challenge #3 Business Intelligence (Core: Search Engine, Dashboards, Asset Service Model)
-
34:55
More cases on our website
-
37:22
Q&A
Some slides from the presentation
We hope you found the webinar useful. Follow our news on LinkedIn and stay up to date with the latest data monitoring trends! 🔥
Follow us
Track and Triumph: The Role of Monitoring System in Modern Business
More about IT Operations
Monitoring IT infrastructure has long been an integral part of business, as it allows you to:
-
– promptly identify and resolve issues before they seriously impact company operations;
-
– enhance performance through smart analysis and optimization of resource usage (from server health and network performance to Active Directory insights and Exchange diagnostics);
-
– track user activity, detect suspicious actions, and prevent security threats;
-
– minimize system downtime due to emerging issues and much more.
IT Operations Bundle offers a streamlined approach to holistic IT management, simplifying the intricacies of monitoring everything from server health to
MS Exchange diagnostics.
About the case
Of course, all of this sounds great. But let's move from words to action and explore the capabilities of such a system using a specific case study.
So, while reviewing
the Asset-Service-Model in the SAF interface, we noticed that the database status indicator was alarming – the average query execution time was higher than expected. This is a clear sign that something is amiss. In the video, we vividly demonstrate the actions taken next and the results achieved during our investigation.
Summarize
By the way,
in this previous article, we also explained how cyber threats are tackled using SAF in a specific case. And
in this article, we demonstrated how SAF can be applied in Business Intelligence.

You can order a demonstration of our product's capabilities and learn more information about it right now 🔥
Why does your company need
the SAF Cybersecurity Bundle?
A little bit about Cybersecurity Bundle
-
Perhaps for detecting, investigating, and resolving issues in IT infrastructure and cyber security infrastructure?
-
Maybe for building user visualization based on correlation rules?
-
Or maybe for retrospective search over stored data for artefacts related to a threat-hunting hypothesis?
With the SAF Cybersecurity Bundle, you don't even have to choose - it covers all these needs thanks to its holistic cyber security monitoring and incident management mechanism. Let's experience all the benefits of this bundle through a practical story.

More about the case
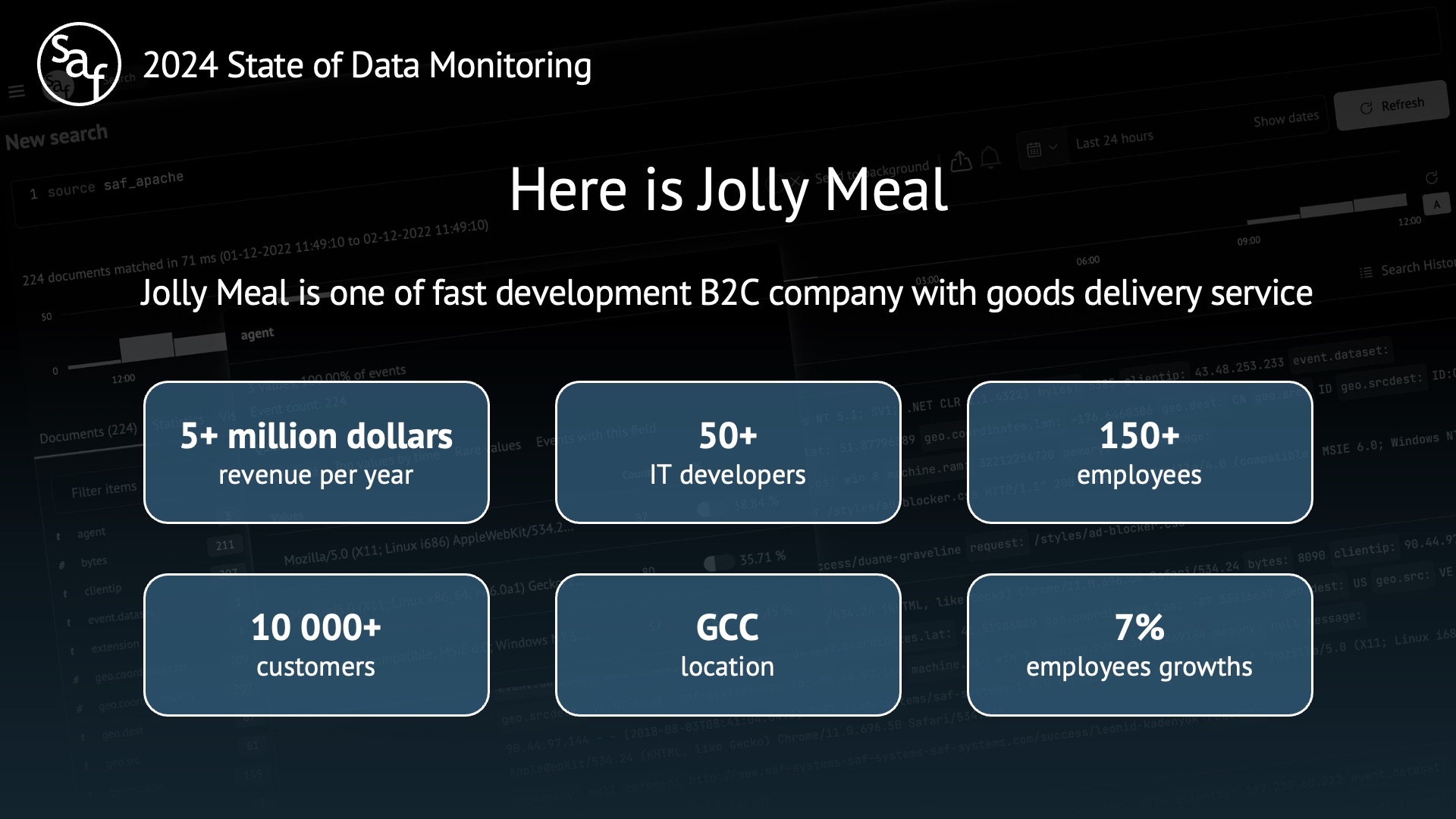
So, we present to you a company with the code name Jolly Meal. It is one of the fast-developing B2C companies with a goods delivery service.

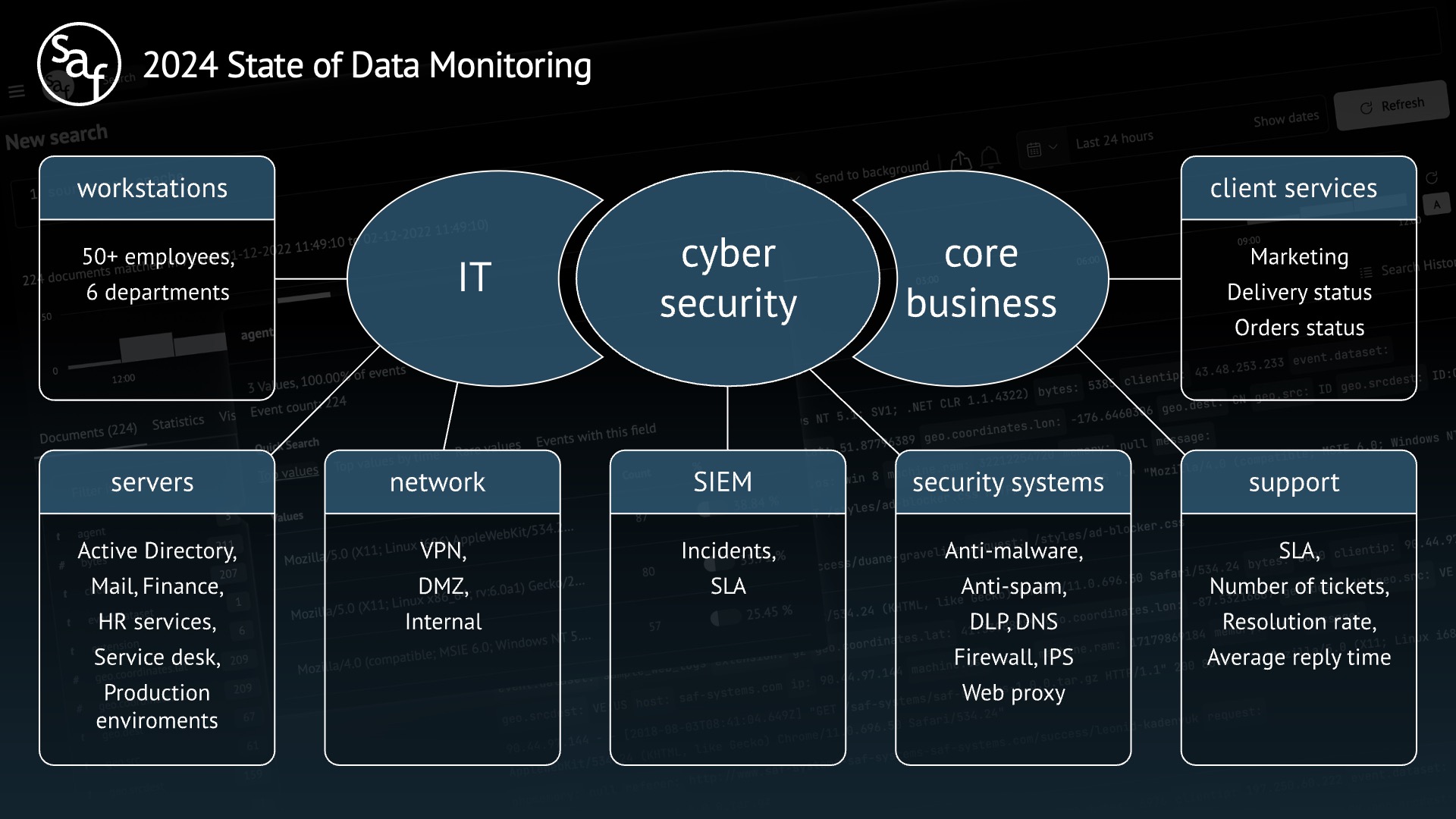
Company infrastructure
To further immerse you in the company, let's take a closer look at its detailed infrastructure.

Let's be in the role of employee
To understand how the Cybersecurity Bundle can help a company, let's put ourselves in the shoes of a Jolly Meal employee.
One beautiful (or not very beautiful) day, we receive a message about a critical event in the Incident Manager. What happened next and how was this problem solved within the SAF Cybersecurity Bundle? Let's find out in the video.

Summarize
-
-
The Inventory module gave us complete information about users, which helped us investigate the incident.
-

Throughout the corporation's existence, it will face cybercriminals and cyber attacks of varying complexity. Don't delay protecting your company - start using SAF today.
If you are interested in the Cybersecurity Bundle, you can contact us to discuss the details 🔥