news
product & company news feed

Machine learning principles. Secure operation
| cybersecurity, AI, NCSC
Machine learning principles. Secure operation
News
Content
Understand and mitigate the risks of using continual learning (CL)
Appropriately sanitize inputs to your model in use
Develop incident and vulnerability management processes
Here we are at the conclusion of the series of articles on the principles of the National…
Machine learning principles. Secure deployment
| cybersecurity, AI, NCSC
Machine learning principles. Secure deployment
News
Content
Protect information that could be used to attack your model
Monitor and log user activity
In today's article, we will discuss the third section of the National Cyber Security Centre publication "Secure Deployment". It will cover the principles of protection during the deployment phase of ML sy…
Machine learning principles. Secure development
| cybersecurity, AI, NCSC
Machine learning principles. Secure development
News
Content
Secure Your Supply Chain
Secure Your Development Infrastructure
Manage the Full Life Cycle of Models and Datasets
Choose a Model that Maximizes Security and Performance
We continue to analyze the article from the National Cyber Sec…

Machine learning principles. Secure design
| cybersecurity, AI, NCSC
Machine learning principles. Secure design
News
Content
Raise awareness of ML threats and risks
Model the threats to your system
Minimise an adversary's knowledge
Analyze vulnerabilities against inherent ML threats
The National Cyber Security Centre has published a comprehensive article on t…
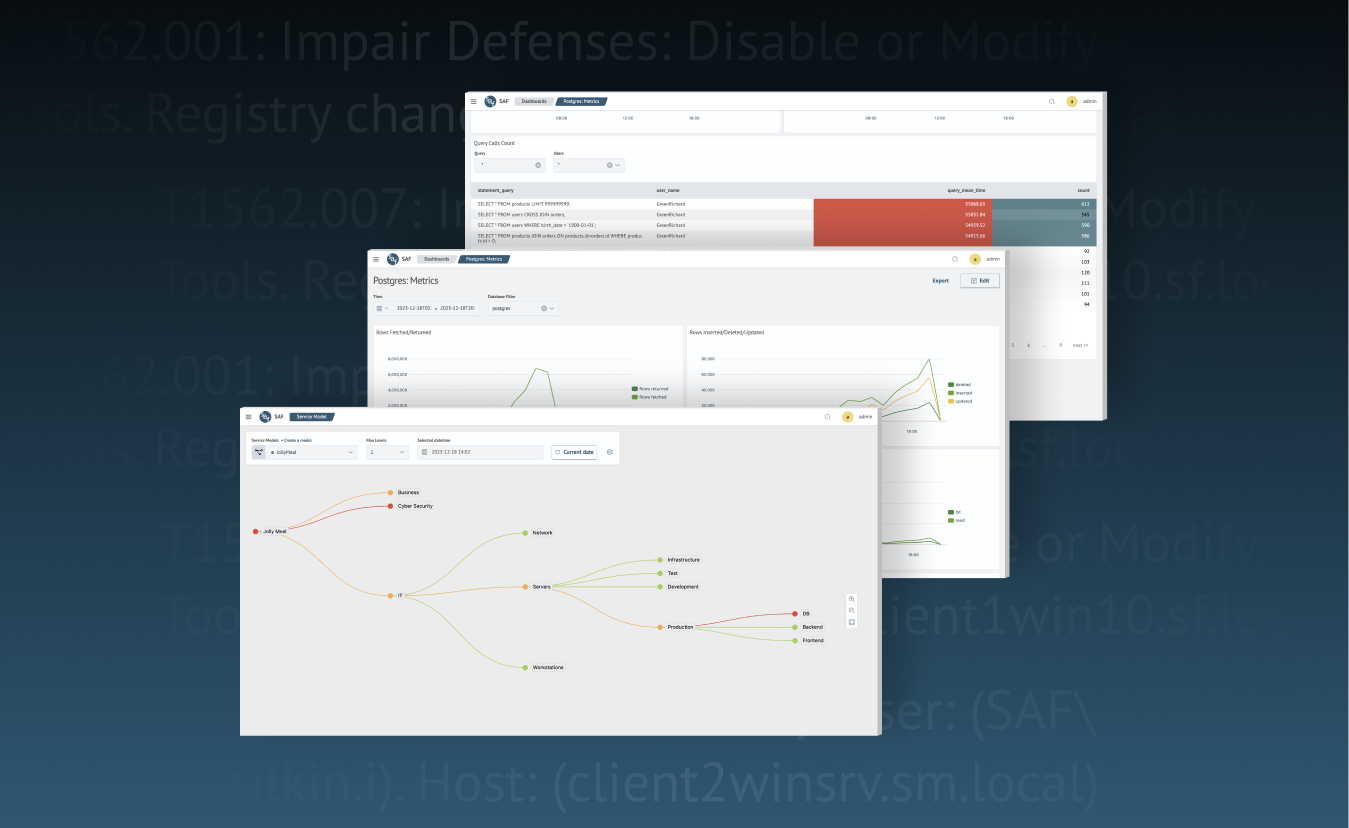
Track and Triumph: The Role of Monitoring System in Modern Business
| usecase, ITOps
Track and Triumph: The Role of Monitoring System in Modern Business
News
More about IT Operations
Monitoring IT infrastructure has long been an integral part of business, as it allows you to:
– promptly identify and resolve issues before they seriously impact company operations;
– enhance performance through smart analysis and optimization of resource usage (from ser…

Top Strategic Technology Trends 2024
| cybersecurity, AI, Gartner
Top Strategic Technology Trends 2024
News
Content
AI TRiSM
CTEM
Sustainable Technology
Platform Engineering
AI-Augmented Development
Industry Cloud Platforms
Intelligent Applications…
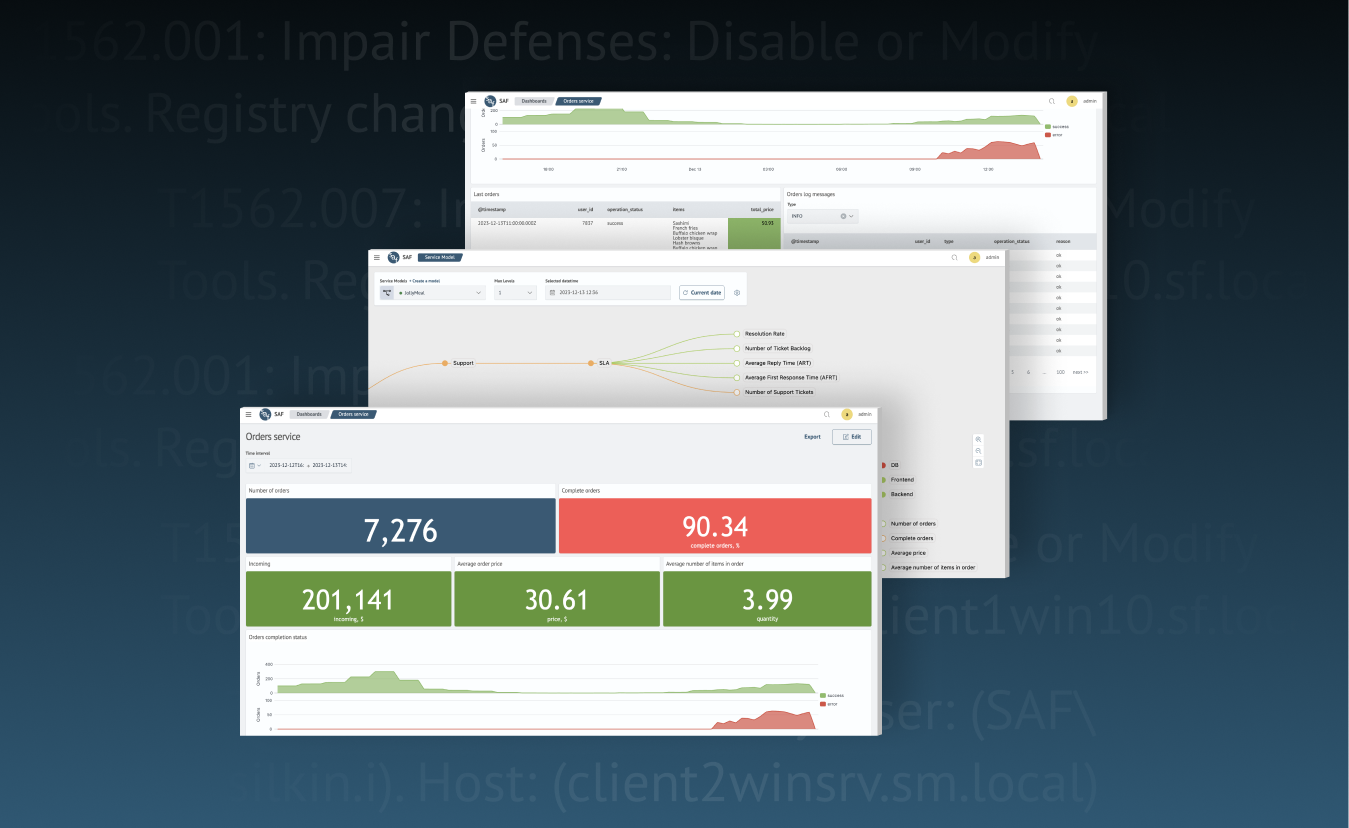
Business Intelligence with SAF
| Marketing, usecase, BI
Business Intelligence with SAF
News
More about Business Intelligence
Data has long been one of the most valuable assets of a company, and using BI is a necessity for successful business development. SAF allows you to effectively track various business metrics and respond promptly to critical changes. All useful information is presented in informative dashboards.
About the case
But let's not talk for long, it's bet…

Ghostwriter or how AI reached technologies of the past century
| AI
Ghostwriter or how AI reached technologies of the past century
News
Engineer Arvind Sanjeev created a smart typewriter Ghostwriter with a language model GPT-3, which responds to user messages and comes up with stories right on paper. To start communicating with this creative gadget or witness the creative process of the invisible writer, just insert paper.
The detailed process of creating this AI creation can be…

How to make AI evaluate your resume at the maximum score
| AI, HR
How to make AI evaluate your resume at the maximum score
News
Recently we came across an interesting material. Artificial intelligence is actively penetrating into all areas of life. It has even reached HR, who have started actively using it to evaluate candidates' resumes. How does it work?
You send your resume to the company;
The company sends the resume text for A…

How will AI become a headache for companies
| cybersecurity, AI, NCSC
How will AI become not only a faithful assistant but also a headache for companies
News
Recently, the National Cyber Security Centre published a report on the impact of AI on cyber threats in the next two years.
What is important to emphasize from this report?
1. Most cybercriminals already use AI in some way in their activities.
2. Cyberattacks using AI are general…

A council for AI in Abu Dhabi
| UAE, cybersecurity, AI
Artificial Intelligence council for Abu Dhabi
News
President of the UAE, Sheikh Mohammed, announced the creation of a council for artificial intelligence in Abu Dhabi. How will this affect data monitoring and cybersecurity in the UAE? Let's discuss.
President His Highness Sheikh Mohamed bin Zayed Al Nahyan
"The council will develop plans and research prog…

Why does your company need the SAF Cyber Security Bundle
| usecase, cybersecurity, SIEM, SOC
Why does your company need the SAF Cybersecurity Bundle?
News
A little bit about Cybersecurity Bundle
Why does your company need the SAF Cybersecurity Bundle?
Perhaps for detecting, investigating, and resolving issues in IT infrastructure and cyber security infrastructure?
Maybe for building user visualization based on correlation rules…

Recording of the webinar 2024 State of Data Monitoring
| usecase, cybersecurity, Webinar
Recording of the webinar 2024 State of Data Monitoring
News
In the webinar we discussed the latest trends in data monitoring and shared our predictions for 2024. We also demonstrated the implementation of these trends in the SAF product using a case study. We would like to thank everyone for their participation and interesting questions.
And for those who could not join us yesterday, we have prepared a recording. You c…
RST Cloud and SAF Systems Alliance
| TI, RST Cloud, integration
RST Cloud and SAF Systems Announce Technology Alliance
News
The other day, Enterprise Security published an article about the RST Cloud and SAF Systems technology alliance.
The collaboration will integrate RST Cloud’s Threat Feed and Report Hub products into our Search Anywhere Framework (SAF) solution, enabling enhances incident detection, facilitates efficient incident triage, and reinforces incident response capabili…

MITRE ATT&CK update
| MITRE ATT&CK, Release
Update of the MITRE ATT&CK module
News
Content
Techniques
Software
Groups
Campaigns
On October 31, 2023, the new 14th version of MITRE ATT&CK was released. We have already implemented the changes into our universal monitoring platform SAF. In particular, the updates affected the MITRE ATT&CK…

Webinar 13 Dec 2023
| Webinar
webinar registration: 2024 state of data monitoring SAF free webinar series
unlock the power of monitoring systems in your company's success
Join us for an exclusive webinar series starting on December 13th, where we will show the potential of monitoring systems in transforming the way businesses operate. Our experts will showcase real-life examples, guiding you through the practical applications that can revolutionize your company's control over internal and external processes.
what…

SAF and Cybersecurity Best Trends
UAE Cybersecurity Best Trends
and how SAF helps to explore them
Based on UAE National Strategy
for Artificial Intelligence 2031 and National Cybersecurity Strategy by TDRA.
Cybersecurity laws & regulations
The UAE government is actively working to establish robust cybersecurity regulations and frameworks, emphasizing data protection, privacy, and secure online transactions. Compliance with these regulations is essential for organizations operating in the UA…

Threat Intelligence
| TI
Welcome to Threat Intelligence Module
News
Content
Threat Intelligence Module
Integration with RSTCloud
Examples
Threat Intelligence Module
The Threat Intelligence Module of the SAF is a tool that collects, analyzes, and provides information about various types of cyber threats and is actively used to ensure the securit…

GITEX is coming!
| GITEX, Conf
GITEX is coming!
News
Exciting Updates! 🔥
Are you ready for GITEX 2023 Largest Tech & Startup Show in the World? We are! SAF Systems is thrilled to welcome all interested companies' representatives during this year's event in Dubai, and we look forward to connecting with you from October 16th-20th. Come visit our booth in Hall 25, Booth D73, right near the Cybersecurity Main Stage. We have some new incredible technolo…

Welcome to our use cases page!
| usecase, projects, success stories
Welcome to our use cases page!
News
We are pleased to announce the launch of a new page on our website dedicated to publishing use cases for our SAF product. Now, anyone interested can explore brief descriptions of successfully completed projects, their objectives, and key outcomes.
use cases base

SAF-System open price list
| Pricing
SAF System open price list has been published
News
Content
Tailored Precision, Cost Efficiency
Empowering Innovation, Minimizing Cost
Enterprise Power, SMB Pricing
Limitless Scalability, On Your Terms
Unlock the true potential of your data, effortlessly manage your IT transformation needs, a…

UAE Cybersecurity Compliance
| UAE, Compliance
Compliance with the requirements of the UAE cybersecurity regulations
News
🇦🇪 UAE Cybersecurity Compliance
UAE National Cybersecurity Strategy
TDRA Regulatory Policies & SIA (Ex NESA) Regulations
UAE Information Assurance Regulation by TDRA
Related standards (NIST 800-53, ADISS v2, SANS 20, ISO/IEC 2700x…

GENTEC
| Conf, UAE, GENTEC
The GENTEC Cyber Security Forum
News
SAF took part at Gulf News GENTEC Cyber security Forum 2023 as a Strategic Partner! ✊ We were happy to meet you here and discuss cybersecurity monitoring. GNTEC Cybersecurity Forum 2023 brought together influential minds and heads of businesses, as well as stakehold…